One of the stranger malware delivery methods I’ve heard of, so let’s talk about it!
On February 16th, 2024, Reddit user VegetableLuck made an interesting (and now deleted) post on the r/malware subreddit, claiming to have found malware when they plugged in a USB vibrator. The post blew up, and though it’s veracity has still not been fully confirmed, it’s honestly really funny. I’ve now had over a week to think on this, and I even went and purchased two of the vibrators in question myself, which has lead me to be 95% sure that this is either a hoax, or misattribution. Why am I being such a buzzkill? Well, I just feel like it. Plus, I’m seeing a lot of misinformation floating around re this subject, and misinfo in cyber is something that I will fight against whenever I can.
The Vibrator
VegetableLuck claims the vibrator in question is the hilariously named Pussy Power 8-Function Rechargeable Bullet Vibrator, purchased from the novelty store Spencers. How exactly could a vibrator deliver malware? Well… if your vibrator looks like this, it’s basically just a thumb drive!
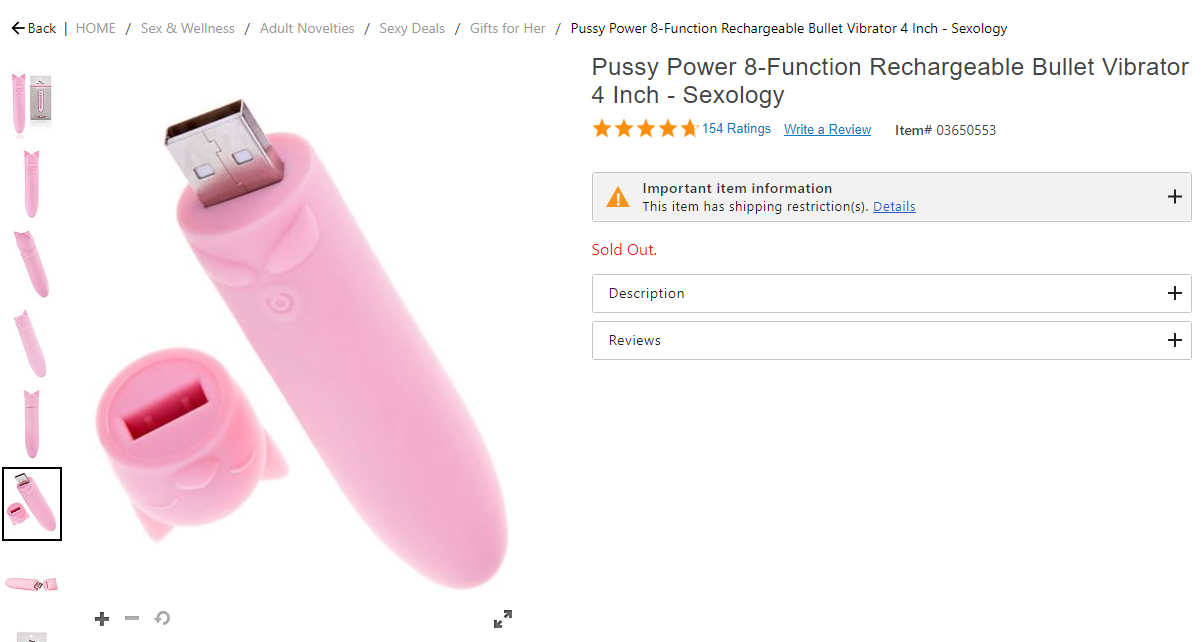
Unfortunately the vibrator is sold out online, but myself and others have traveled to their local Spencers to purchase the device for themselves. Repeated attempts by me and others to obtain the device from the OP went unanswered, meaning we must rely on devices that are almost certainly manufactured at a different time than the OP’s.
Still, it’s bizarre to look at, isn’t it? Something about this incredibly cursed flash drive makes my two wolves feel very different feelings.

The Post
Let’s look at the post and see how VL claims they obtained the malware.
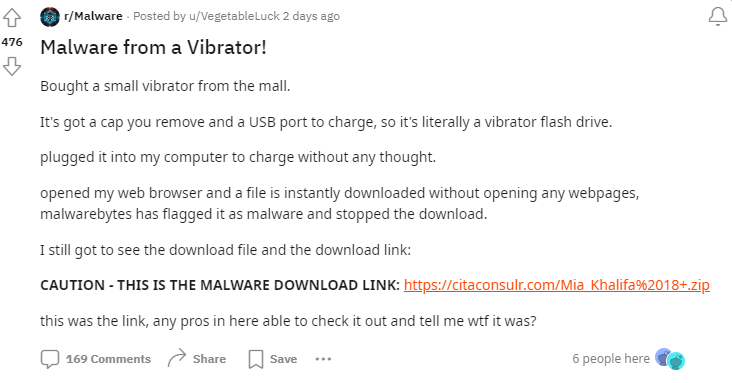
At this time, I’m uncertain if they meant that they opened the web browser and the file was downloaded, or that the web browser opened on it’s own. Regardless, this doesn’t have a strong effect on my conclusion.
The malware in question was found to be Lumma Stealer, a classic infostealer.
USB-Based Malware Delivery
Lets go over how exactly a USB drive could deliver malware, as understanding how this malware would have had to be delivered impacted my opinion on the veracity of this post.
First, there’s the concept of autoruns. A device with autorun would essentially execute whatever program it wanted upon plugging it into your computer. This device could be CDs, DVD, USB drives, or even a server share. This was dangerous and a common malware infection vector, so Microsoft actually disabled this feature in Windows Vista onwards. XP’s market share dwindles every year, so I’m going to take a guess that OP is not on XP.
Now, there’s another option, as I mentioned above. This is known as a BadUSB. A BadUSB essentially appears as a USB keyboard when plugged into a computer, which then types out commands. Basically, assume that a badUSB being in your computer is just like if a threat actor had terminal access under your user account’s privilege level.
If OP is to be believed, then we’ll assume that the malware vibrator is a BadUSB. So, let’s talk about how that may have been placed into the vibrator.
Supply Chain Shenanigans
Imagine the spencer’s sex toy factory. Like any good factory, you buy most of what you need in bulk from other suppliers. That likely included the generic hardware components of the devices, like the control switches, vibration units, and yes, the USB charging ports. So, you regularly receive massive orders of tens of thousands of these components, and you just install them into devices and ship them off. That’s the way it goes.
Now, we know that not all of the devices coming out of the Spencers sex toy factory have malware, because this story would be a lot bigger right now. So, we assume that a malicious actor within the factory that manufactured these USBs, or someone else along the chain of manufacture to delivery, must have contaminated the supply of USBs with the BadUSBs. Now, think about the supply chain. We don’t really know when these devices were created, but it’s safe to assume that it’s likely a few months at least between the BadUSBs being placed into the supply chain, and the devices arriving to consumer’s houses.
That’s a lot of work. Work, and investment. And risk! There are much easier ways to infect someone with malware. But still, we’re going to assume that what I’ve just describes is roughly what happened.
Now, I’m going to tell you why I think that something doesn’t add up here. I’m about 95% sure that this is either a hoax, or the zip file being downloaded was a coincidence, caused by something else. Although, I will also talk about the infection scenario that I think makes the most sense, if this was legitimately an infection because of a BadUSB vibrator.
Put yourself in the mind of a threat actor, criminal, a bad guy. You’ve found the perfect scenario to get a malicious device into the supply chain. It wasn’t easy or cheap, and there’s risk, so you want to ensure that you get the highest payoff for your investment. An infostealer makes sense, although I’d personally go for trojan dropper in this situation. Now, you have two options. Since it’s a BadUSB device, you can essentially run most or any commands. You could install the malware completely quietly, with the user never knowing anything is wrong unless their antivirus detects something. But, the badUSB could also potentially disable the antivirus first. That’s the most efficient delivery.
Instead, the malware opened up the web browser, connected to a website, and downloaded a ZIP file. For the malware to run, the victim needs to unzip the folder and run the undisguised program. Some people in this scenario would run the program, but many would not. This means that the first infection method would have a much higher success rate than the second. And I just cant believe that someone would go though all the effort to introduce the BadUSBs into the supply chain, only to use such an inefficient infection vector. It just doesn’t add up to me, and therefore, I don’t believe that the vibrator actually was responsible for the events that OP described in the reddit post.
Now, I think there’s a small chance that, if we do believe that the vibrator was actually infected with malware, that the opening of the web browsing was a red herring or a secondary infection method if the malware could only run elevated and the account was standard. Still I don’t think that’s very likely. The OP didn’t mention Malwarebytes catching anything else, and MB is a very good product.
Conclusion
Well, that’s my thoughts on this whole situation. I’ve been thinking about this for basically this last week, doing some research, and I think I’ve come to a conclusion that makes sense to me. But hey, maybe I’ll be proven wrong some day!
Thoughts? Opinions? Want to tell me I’m an idiot who misunderstood the topic? Leave a comment, send me an email, message me on LinkedIn, whatever you want. Thanks for reading!