This article serves as another place to document some common (and not so common) Oauth applications that are abused for malicious purposes during a BEC. Some are well documented, while others are rarer, only discussed between responders or detailed on GitHub lists. The places where some of these apps are detailed may only provide a brief summary of the application, while this article aims to provide more information on the potential use and impact of those less common applications.
For more details on the apps such as their App ID and MITRE details, check out the below two links.
https://huntresslabs.github.io/rogueapps
The Masterlist
(Click an application to go directly to it’s entry.)
- PERFECTDATA SOFTWARE
- eM Client
- Newsletter Software Supermailer
- CloudSponge
- rclone
- SigParser
- Fastmail
- ZoomInfo Login & ZoomInfo Communitiez Login
Most Common
PERFECTDATA SOFTWARE
This is one of the most documented and abused applications. In a tenant the application will show up as PERFECTDATA SOFTWARE, but the real software behind it is called Email Backup Wizard. It is a desktop application that allows you to export a cloud mailbox to PST. This activity is classified as exfiltration, and means that all data inside the mailbox is at risk of unauthorized use. I often see the usage of PDS initiate the following:
- Compromised user account consents to application, entire mailbox is exfiltrated.
- A typosquat type domain (such as goggle.com) for the company is registered.
- Existing email chains are replied to via the typosquat domain, in order to change payment details or for other fraudulent purposes.
As most email inboxes will have sensitive information inside, it is important to advise all people and customers/clients that their email conversations with the account are likely leaked, and to not change any payment information without validating the request via phone call.
References:
https://cybercorner.tech/malicious-azure-application-perfectdata-software-and-office365-business-email-compromise/
https://darktrace.com/blog/how-abuse-of-perfectdata-software-may-create-a-perfect-storm-an-emerging-trend-in-account-takeovers
eM Client
eM Client is another commonly seen application. I describe it as an ‘alternative mailbox access client’, meaning that it is an application used to access an email account that is not the usual, such as Outlook or the windows Mail application. My research into eM Client has found it to have several features that make it appealing for a threat actor to use. These include a built-in mass-mail function, covert email downloads (meaning downloaded email cannot be audited), contact export, and a setting so that sent emails are not placed within the sent mail folder.
As activity auditing for eM Client is difficult, I advise clients to assume that all email and contacts within the compromised account, and any shared mailboxes, is at risk.
References:
https://cybercorner.tech/malicious-usage-of-em-client-in-business-email-compromise/
https://www.huntress.com/blog/legitimate-apps-as-traitorware-for-persistent-microsoft-365-compromise
Newsletter Software Supermailer
This application is another desktop application that integrates with an email account. It is used for bulk-mailing purposes, where the compromised account is used to send phishing email, creating more victims. My experience with responding to this application’s usage showed that it was somehow able to bypass Microsoft’s outbound spam filter message limits, which block an account from sending any more mail if it hits a certain hourly threshold. Thankfully, usage of this application has dropped significantly, as it now appears to require administrator consent to be used.
References:
https://trustifi.com/blog/what-is-a-supermailer-email-phishing-attack/
https://darktrace.com/blog/business-email-compromise-to-mass-phishing-campaign-attack-analysis/
Generic Registered Applications
There exists the capability to register a custom application within a tenant, and by default this action can be done by any user account. If a user registers a custom application, it can still have full access to the user’s account and with the user’s access rights. I have personally seen this activity a handful of times, which occurred during two timeframes.
The first timeframe was in July 2023, and the application would be registered with the name “App” and the permissions ‘Mail.Read.Write’, ‘Mail.Send’, ‘User.Read’, and ‘offline_access’. The second timeframe was Feburary/March 2024, and the application was registered with the name “test” and the permissions ‘User.Read’, ‘Mail.Read’, ‘Mail.ReadWrite’, ‘Mail.Send’, ‘People.Read’, and ‘offline_access’.
The ‘test’ application was created with the Azure CLI, which tells me that a script of some sort is used to create the actual ‘application’. Once the application is created, my assumption is that a custom application that exists as a CLI or GUI is used to carry out a variety of malicious activities. During both timeframes I attempted to locate the source of the script or information on who was responsible, but I was unable to do any attribution.
Microsoft did publish an article on the “App” application, which is linked below. It’s one of the best written on the subject, so if you read any article linked from this blog I suggest you read it.
References:
https://cyberdom.blog/persistence-via-app-registration-in-entra-id/
https://www.microsoft.com/en-us/security/blog/2023/12/12/threat-actors-misuse-oauth-applications-to-automate-financially-driven-attacks/
Less Common
There are other apps used during a BEC that responders dont see as often, including some that I can find only one mention of, or that I have only experienced once.
CloudSponge
If you google CloudSponge you’ll likely fall down the rabbit hole of some sort of contact gathering thing. Not what we’re looking for, exactly. After some searching to find any record of folks testifying to the malicious usage of CloudSponge, all I could find was the list on GitHub that I reference for my Osprey PowerShell module. The list says that CloudSponge is used for address list exfiltration, so lets try to google “CloudSponge Export Contacts” and see what we can find…
Very nice. Google once again proves itself to be the most useful tool in my arsenal.
So what exactly does it do? Well, follow the GitHub page to the website, and you’ll see that you can link the site to a 365 account via an app consent, grant it permission to view your contacts, and watch as it spits out a nice list. Perfect for extracting your contact list when sending phishing!
It’s hard to find anyone vouching that they’ve ran into this during an investigation. I’ve yet to encounter this in the wild, but this activity seems realistic to me. Actually, Now that I’ve found this, it would have been way easier to use this to export all the addresses from an inbox when doing breach notification than the suffering I went through using MFCMAPI and Notepad++… Don’t ask.
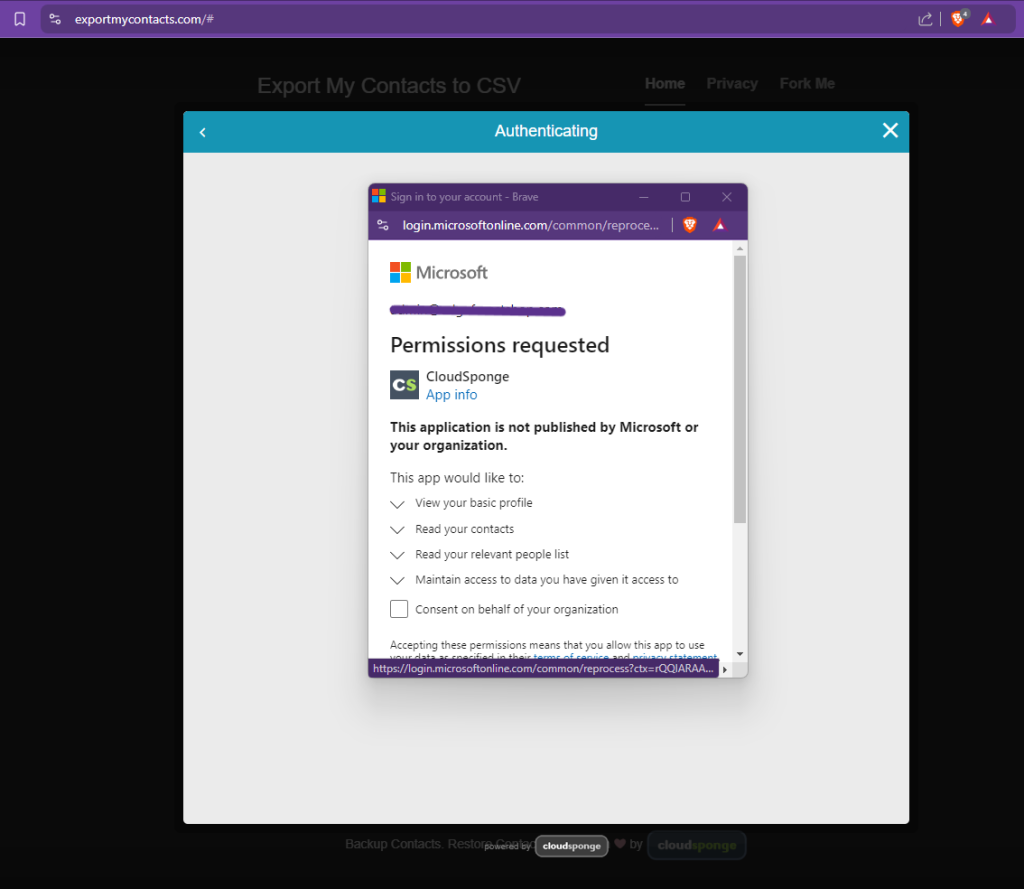
References:
https://www.exportmycontacts.com/
rclone
rclone is a free utility that can be used to manage files in cloud storage, including OneDrive and SharePoint. It runs from the CLI and is very versatile and powerful. In the context of threat actor activities, it’s used to exfiltrate files from OD/SP.
References:
https://dfirinprogress.com/posts/data-exfiltration-m365-rclone/
https://www.kroll.com/en/insights/publications/cyber/new-m365-business-email-compromise-attacks-with-rclone
https://attack.mitre.org/software/S1040/
SigParser
SigParser is used for exfiltration and ‘lead generation’, and once connected to an email account, will build out a profile of the contacts and companies the mailbox interacts with. It does this via a range of permissions, including access to emails, contacts, and calendars. This activity is similar to CloudSponge, but more sophisticated. For example, SigParser can tell you the most common companies that someone would interact with, allowing you to better target your malicious activity. No more digging through the inbox to find the most common business partners, SigParser does it for you!
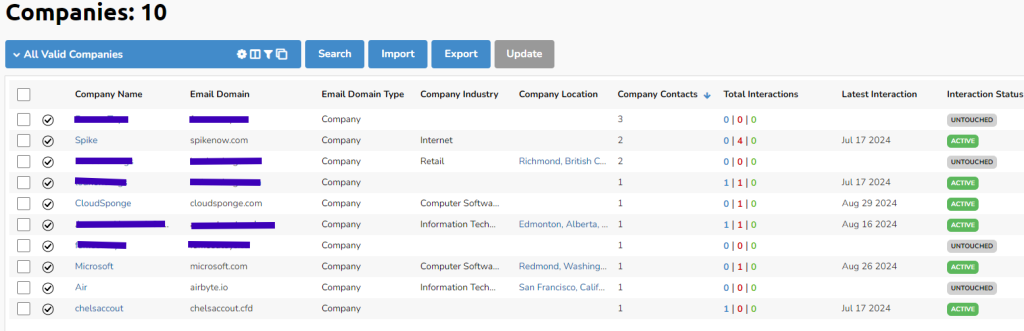
Fastmail
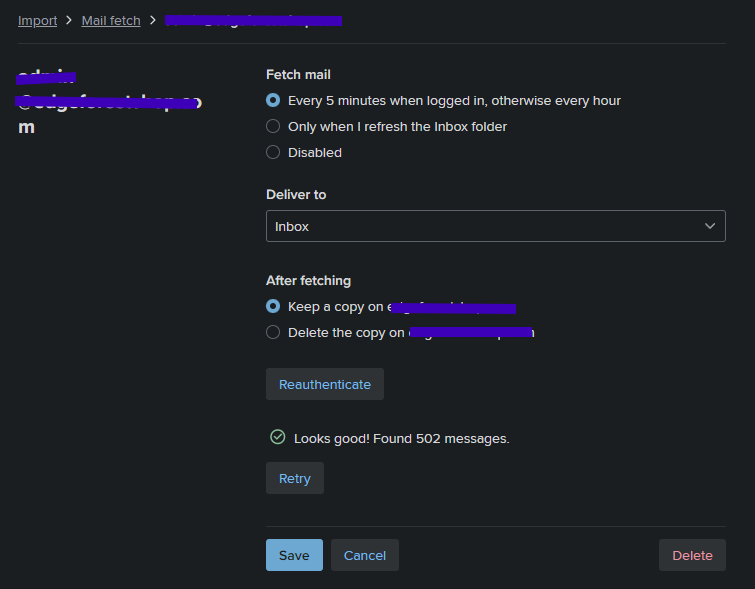
Fastmail is a private email hosting service. Consider it a smaller competitor to Gmail, Outlook, etc. A Fastmail account is free to create and use for 30 days, then you must pay for it. Upon creating a Fastmail account, you can choose to import emails from various services including Microsoft365. You connect to Microsoft via an application consent (permissions vary depending on if it’s an admin consent or not, interestingly) to start importing emails. There is also an option to continue to sync emails into the service periodically. This is a classic case of Exfiltration and Persistence. All emails are stored offsite, so even if the threat actor looses access to the inbox, they still have the emails. Persistence technically exists here as well, but Persistence with M365 OAuth applications is… weird. Varies on the exact permissions used, how the application was programmed, etc. Sometimes a password change is enough to cut access, other times it’s not. More research is needed into application permissions and token revocation.
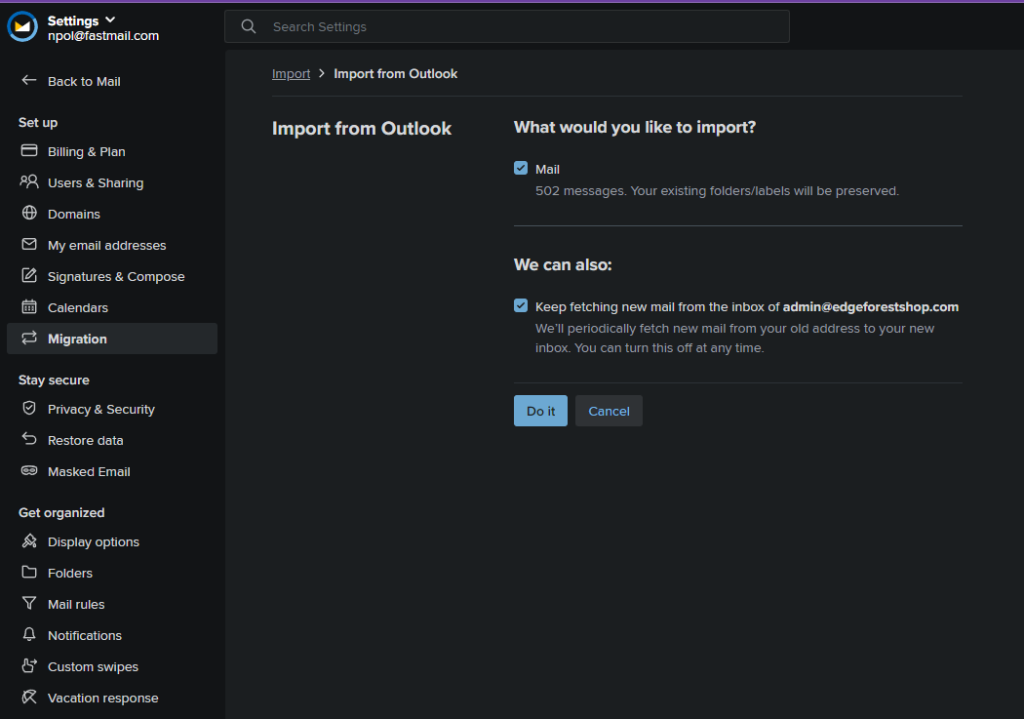
References:
https://www.fastmail.help/hc/en-us/articles/360060590593-Migrate-to-Fastmail-from-another-provider
ZoomInfo Login & ZoomInfo Communitiez Login
ZoomInfo is a well-known commercial data brokerage and B2B contact discovery service. ZoomInfo can be used to find information about businesses and their employees, which would be useful for a threat actor when they are doing reconnaissance or searching for phishing targets.
I have seen two ZoomInfo-related applications used during a BEC incident. The first, ZoomInfo Login, means that a traditional OAuth-enabled account creation occurred, such as by creating an account at a website with your Office365 account. This allows the threat actor to use the compromised account to access ZoomInfo with a clean, free tier account. A free account allows for a certain number of information lookups.
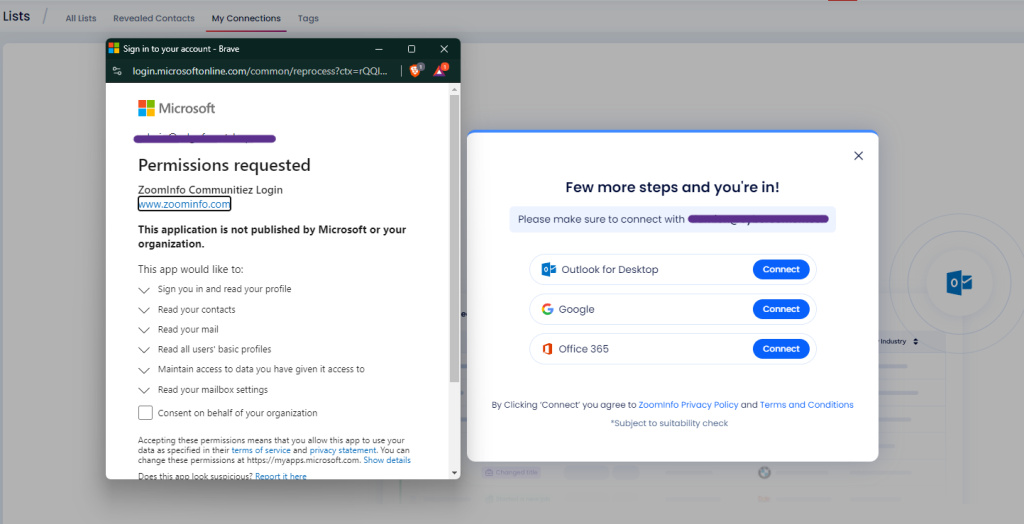
ZoomInfo Communitiez Login is consented to when an account uses the ‘Lists’ feature within ZoomInfo, and selects the option to view ‘My Connections’. Similar to other contact aggregation services such as SigParser and CloudSponge, this builds a list of contacts from various sources within the account, allowing for easy contact discovery, exfiltration, and phishing.
References:
https://abnormalsecurity.com/blog/cybercriminals-exploit-b2b-lead-generation-tools