Edit 04/13/25: The newest version of the software behind this application has changed. Now, the application’s name within a tenant will be Mail_Backup. The app id is now 2ef68ccc-8a4d-42ff-ae88-2d7bb89ad139. Most of the information contained in this article is still accurate. Please view this post for up-to-date IOCs and permissions for this app.
If you have found your way to this page, you likely discovered a suspicious application consent within your Azure AD tenant for an app called PERFECTDATA SOFTWARE. Concerned, you googled the application (and perhaps even its Application ID ff8d92dc-3d82-41d6-bcbd-b9174d163620) looking for information. As of the time of writing, two other results on Google involve this software and BEC. If you haven’t, I encourage you to read this darktrace.com article which goes further in-depth into a Microsoft 365 business email compromise (BEC). Unfortunately, Darktrace was unable to conclusively determine the purpose of the application consent. Luckily I have been able to find the application and examine its behavior.
The TL;DR
First, if you are seeing this application in your tenant and it’s not approved, I have some bad news. This application is used to take a backup of the entire mailbox from the cloud and export it to PST. Assume that everything within the mailbox is lost, and any useful information will be used for future fraud or sold on the dark net. Oh, and if it was an administrative user compromised? It could potentially be every mailbox within the organization.
I’m sorry if I just ruined your day.
Applications Within Azure
An application can integrate with Microsoft 365 and Azure to do many things. The majority of applications that integrate with Azure do so for OAuth purposes so that you can sign into them with your Microsoft 365 credentials. Other applications integrate with Azure to provide you with a service, such as adding appointments created in a third-party app to your Microsoft 365 calendar. For those applications to access your Microsoft 365 account and its data, it must be granted the necessary permissions.
Perfectdata Software is an application that integrates with Microsoft 365/Azure to provide a service, as detailed below.
The Hunt
To begin, I will show you how I went from seeing this application within a tenant to learning what it does.
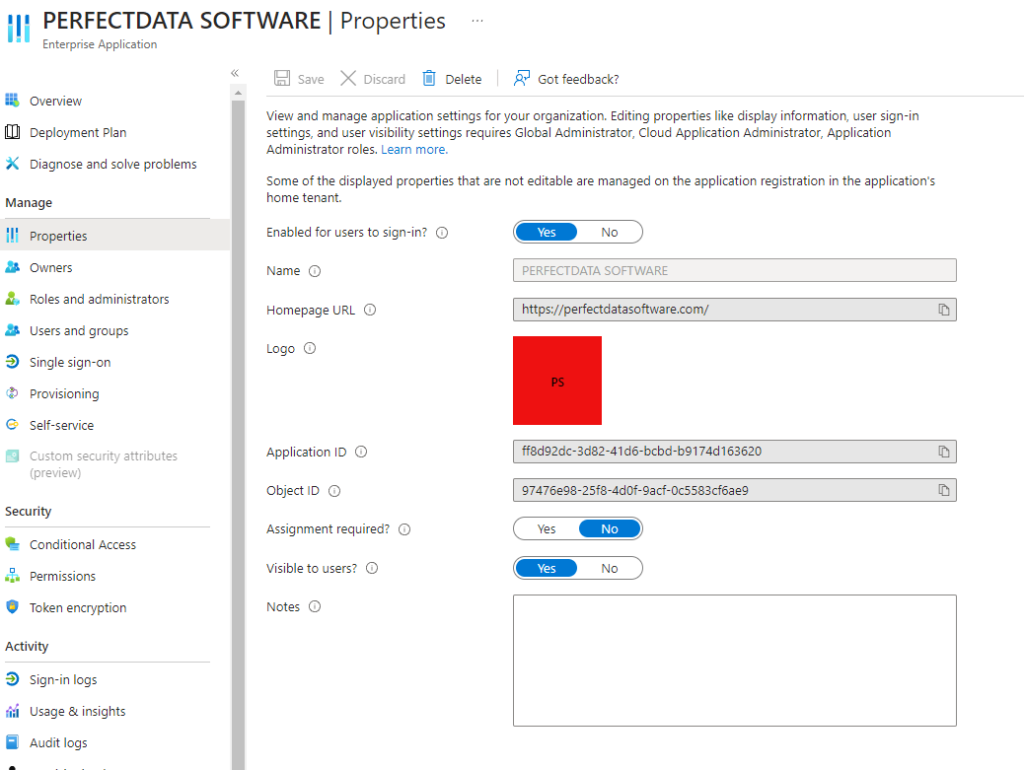
This is what you will see when viewing the application. Now, going to the website listed as the homepage URL takes you to a company that does data recovery and email conversion.
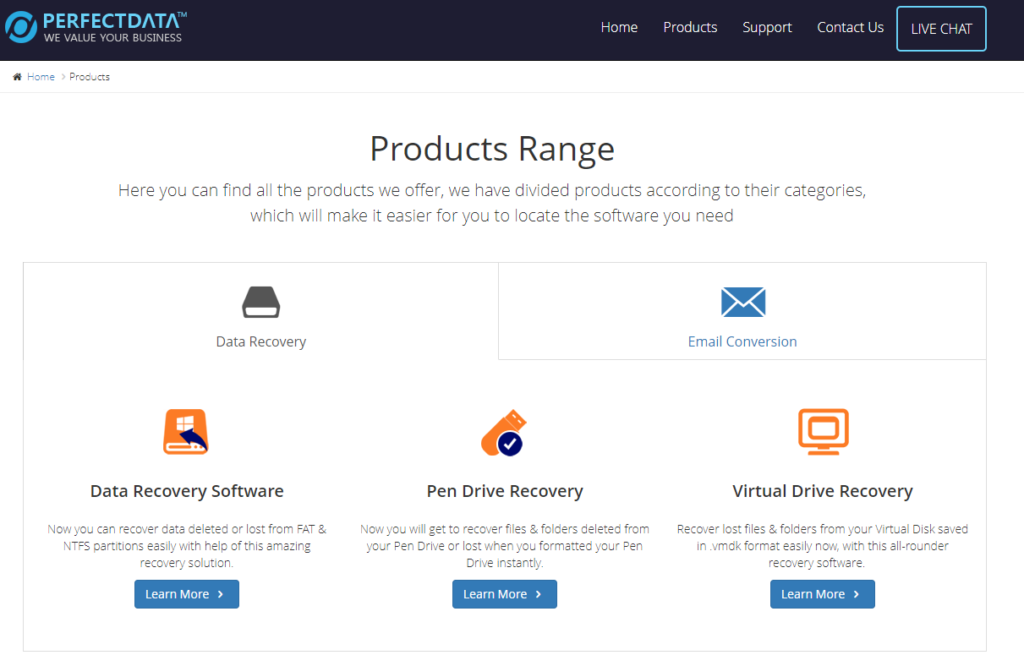
Hmm… not quite what I’m looking for.
Next, I decided to use one of my favorite OSINT tools- Google. I searched for site:perfectdatasoftware[.]com and oh boy, I got a lot of results. I’ll eventually do a deep dive into this company, but to keep on track I found that perfectdatasoftware[.]com has many subdomains that redirect to other companies. This is the one that caught my eye, and it ended up being my lucky break.
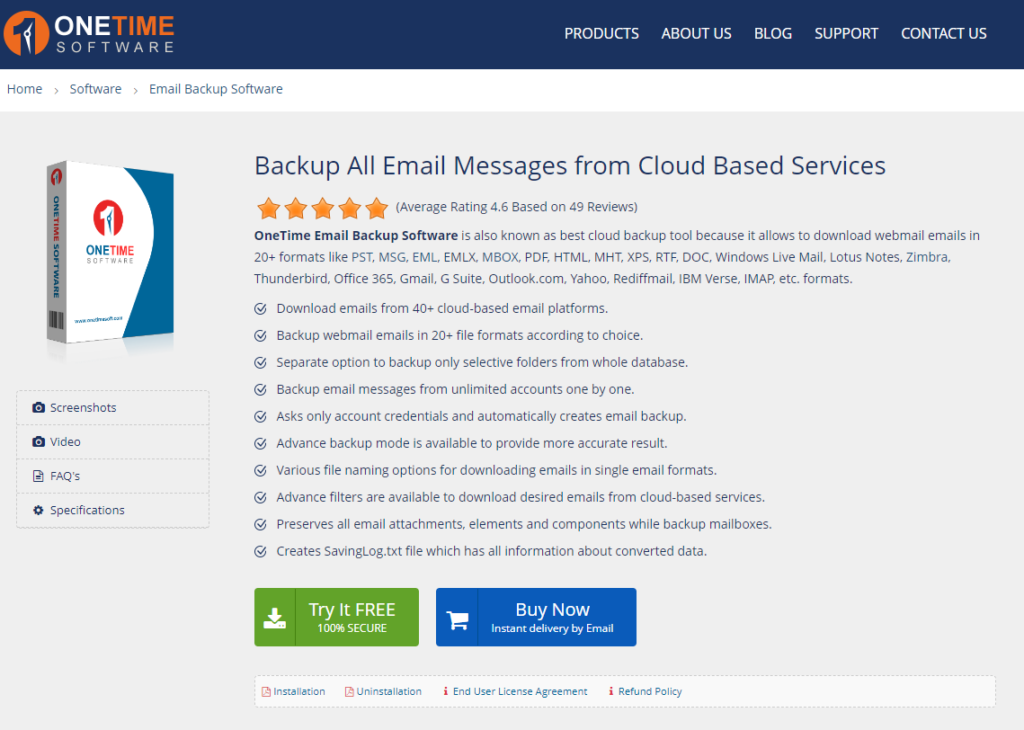
Let’s try this. I downloaded and installed the application, and upon opening it, was prompted to choose my cloud email provider and enter my credentials.
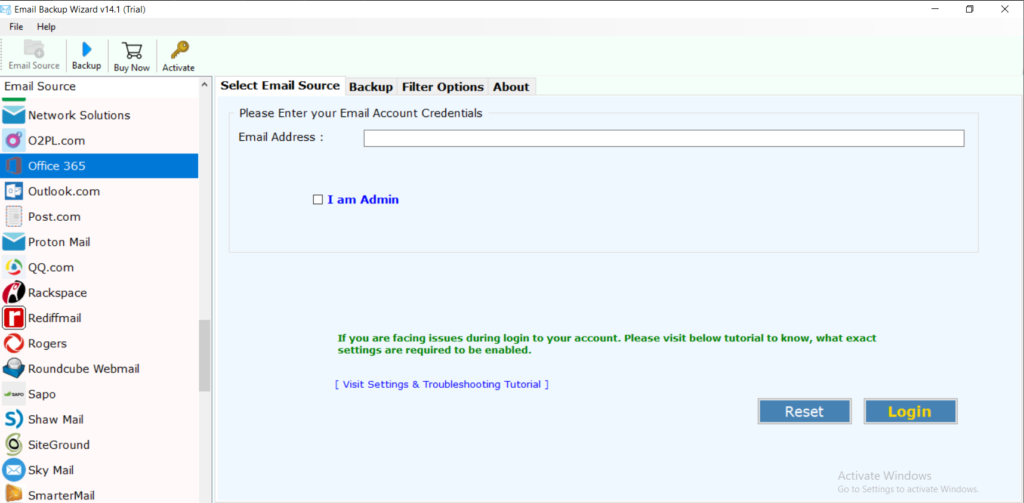
After entering my email, I am provided with the modern Microsoft 365 login. I enter my password, click sign in, and am presented with an application permission request.
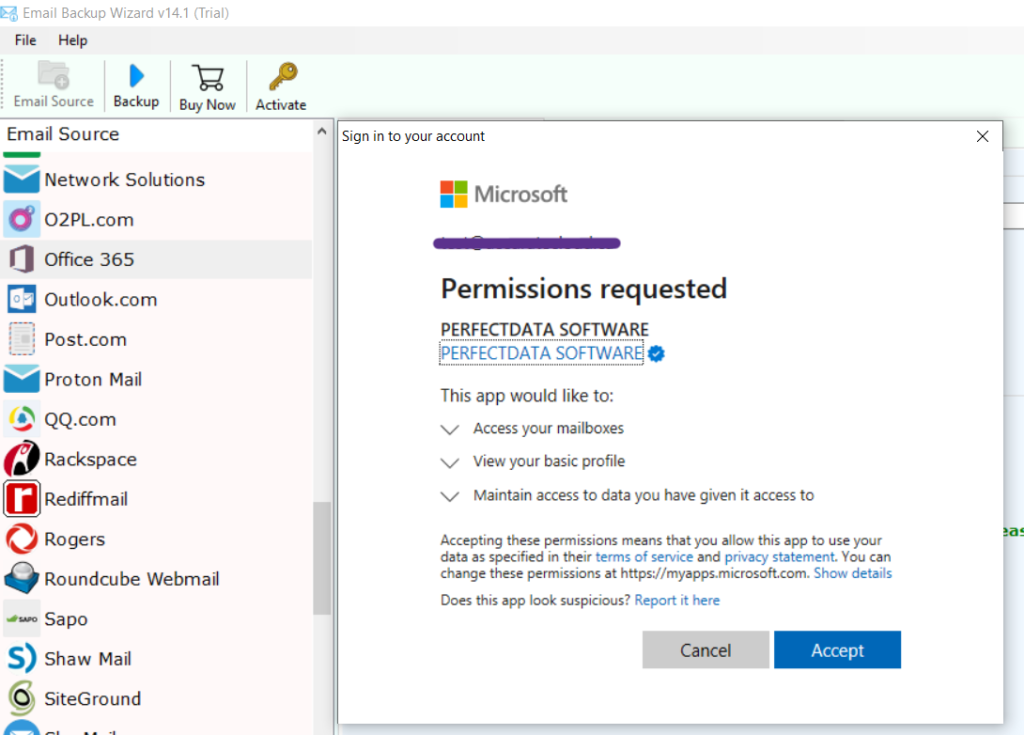
Jackpot. After clicking accept, I am told to wait while it analyses my account. Finally, I am shown my Microsoft 365 folder, and the option to export it to PST. Since it’s a PST, it grabs calendar events and contacts on top of emails and attachments.
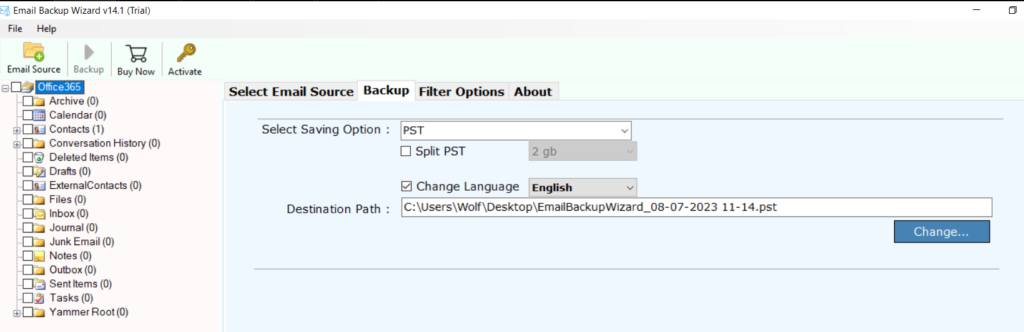
And just like that, I can exfiltrate the mailbox offsite.
After testing, I was able to confirm that the application ID inside my test tenant matched the application ID I had seen in the BECs utilizing this application.
A Deeper Dive
As I have shown, when you see this application within your Microsoft 365 environment you should assume that the entire contents of the mailbox have been exfiltrated. Quite the privacy breach, no? Now, there’s still some good news. My testing has shown me that this tool cannot be used to back up mailboxes that the user has delegated access to. Some tools do that (so you should run access reports on delegated mailboxes that the compromised user has access to) but this is not one of them
Now, remember what I said about administrative users? Well, this tool will allow an administrative account to back up as many mailboxes as a person wants.
The provided documentation says that MFA must be disabled, the account must have application impersonation rights, and it needs delegate access to all mailboxes it wants to back up. I was able to get an admin account with MFA to back up mailboxes, as well as an administrative account that only had application impersonation rights.
If your tenant has access to the MailItemsAccessed record for the account in question, you may see that record with the service principal ID of the application. This isn’t always the case, and since that record is less than helpful you should always assume all the email has been stolen.
What Now?
What you do now depends on your experience, the data involved, the scope of the issue, and any legal or compliance requirements/legislation that you must comply with.
First, do not delete this application from your tenant. You can go to the application within Azure, go to it’s permissions, and click review permissions. If you designate the application as malicious, Microsoft will provide some handy PowerShell scripts for dealing with the application. It’s important to disable the application but leave it in the tenant, as that will prevent anyone from being able to use it in the future.
If you believe that an administrative account was compromised, it’s important to search through audit logs for any activity. Microsoft offers some guidance on dealing with an email compromise, which includes limited details about administrative account compromises. I personally use either the HAWK forensics tool or my own PowerShell module Osprey when investigating BEC, and it gathers helpful information about the tenant as part of it’s initial tenant investigation. Unfortunately, those two options might not be enough. If you are a SMB dealing with this problem, then you should consider contracting third-party forensics.
You should also understand your requirements around compliance legislation. In Canada, any suspected privacy breach needs to be reported to the Privacy Commissioner. If there is a risk of harm related to any stolen personal data, those affected must be notified of the breach. Other countries have similar legislation, but it’s up to C-suite and Legal to determine next steps for those matters.
Finally, this is your sign to make some security improvements to your tenant. Azure AD/Entra ID Premium P1 or P2 are great, so choose licensing that includes one of those. You should also turn on administrator consent requests for risky applications. This prevents end users from granting an app access to more than it should have and allows you to review applications that have been added.
No matter the technical controls you put in place, alerting is very important. The most recent time I responded to a BEC including this application, was because I received an alert for it. There are plenty of tools for both SMB and Enterprise that have alerting for cloud email systems.
The Actual TL;DR
Having this application within your tenant is not a good sign. It allows a threat actor to exfiltrate the entire mailbox as a PST. If the threat actor has access to an administrative account, they can exfiltrate every single mailbox within the organization. This data includes all emails, attachments, calendar events, and contacts. The impact of this activity depends on the scope, what data was in the mailbox, and your compliance requirements. Limiting end user consent to applications can help prevent malicious application consents from affecting your tenant in the future.
Need Help?
If you read this article and have now come to the conclusion that you are experiencing an email compromise, it’s normal to feel scared or uncertain, especially if you’ve never dealt with something as serious as this before. I have provided a guide for investigating an email compromise, so give it a look if you need. I can also be reached via LinkedIn, Email, or Discord to answer questions.
Unrelated Final Notes
If you like what I do and found this post helpful, please consider buying me a coffee on Ko-fi so I can continue to do more things like this.
This is the first blog entry/article I have written, so if you have any feedback I would appreciate it. I will update this article whenever I discover new information.
Thank you for reading my post!
Just had a user report weird MFA activity and it lead me here…THANK YOU for this post. It has been extremely helpful.
You’re welcome! Good luck with your remediation. If it helps, I also have a guide for investigating business email compromise on this blog.
Pingback: Defend your Microsoft 365 accounts: Navigating the surge in attacks and how to shield your business | Sherweb
Thank you for this post, really helpful. And your post on handling BEC, again, excellent information.
I’m just working through this exact issue with PerfectData software application. Do you know if any logs are left in O365 to show if PerfectData has downloaded the user mailbox or not?
Hello, thank you for reading!
Unfortunately, even with E5 licensing I was unable to find any logs in the tenant showing mailbox download. Since it’s pretty much a single-use application, that’s why I mention to assume the worst.
Good luck with your remediation.
Hello, I had the same issue and I found that MS Purview in the audit section allows me to drill into the Exchange Online logs and there I found the evidence of the access made to the mailbox from the same IP that made the MFA Access
Ha, you beat me too it. I found last week that the MailItemsAccessed record would show access from PDS with the same IP and service principal ID.
can you tell me, did the application give you access to shared mailboxes, delegated mailboxes, or Public Folders when connected to the user mailbox?
If the account used to connect is an account without Admin permissions, then I don’t believe that it can access shared mailboxes, delegated boxes, or public folders. I just tested and was unable to see any of those in the folder structure that the application showed me upon export.
Unfortunately, there isn’t a direct way to view detailed activity logs for specific Azure Enterprise Applications within M365. However, you can leverage Azure Active Directory (Azure AD) to gather insights into their sign-in and permission usage. Here’s what you can access and the licensing requirements:
Available Logs:
Sign-in Logs: These reveal user and application sign-in attempts to your M365 tenant.
Directory Audits: These logs capture administrative activities related to Azure AD, including permission modifications for Enterprise Applications.
As you mentioned there are licensing requirements to access some of the logs I mentioned but the core requirement is Azure AD Premium P1/2 (aka Entra ID Premium P1/2). Sign-in Logs and Basic Directory Audits: These are available with most M365 subscriptions that include Azure AD functionality (e.g., Business Premium, E3/E5).
While these logs provide valuable information, they won’t show what actions the Enterprise Application performs within M365 services (like mailbox access).
For in-depth usage logs specific to an Enterprise Application, you might need to consult the application’s documentation. Some applications offer their own auditing mechanisms. Hopefully Microsoft will make changes to give deeper insights, such as API calls, commands issued, services interacted with/modified, etc. in the future but for now you’ll have to rely on 3rd party solutions.
what if i already deleted the app? is there any way to look at the app as it was before i deleted it, whether in audit logs or elsewhere?
Yes, you can view information about the app by going to the user in Entra and clicking on the Audit logs tab. You are looking for the below results, provided the activity was within the last 7 or 30 days depending on your audit log retention.
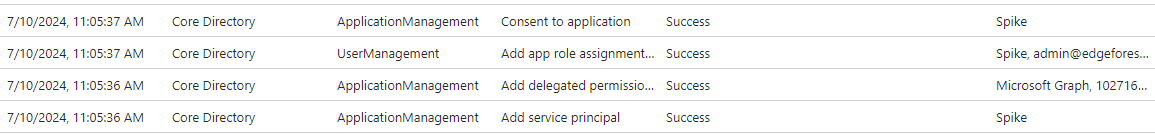
If you click on those logs, you’ll see information such as the permissions and other details.
The same information can be found within the Unified Audit Logs. I detail some info about finding these in my BEC guide.
Question
How does this bypass MFA. Got a lot of User using MFA and are still falling to this issue
MFA is most often bypassed via AitM Token Theft, as detailed here, here, and here where I show the process of stealing the token to exfiltrating emails.
There are a few ways to protect against token theft in M365, including the Identity Protection features, token protection specific conditional access policies, and what I refer to as an “Intune lockdown” where you enforce devices being enrolled in Intune MDM and lock down the enrollment, and then block access from non-Intune devices.
Some hackers can access the E-Mail account of M365 with MFA enabled via this software.
besides disabling/deleting this enterprise app in MS, and resetting the password and MFA settings for the end user, are there any other steps to take to re-enable the ability for the end user to access their account and continue using it as normal, moving forward?
Have you checked out my guide on investigating? Remediation is really going to depend on the activities that took place, but another good place to check is for any inbox rules and to recover any emails that may have been deleted. Other than that, you’ve gotten the main points.
Is there anything that will show in the UAL about syncing if this tool is used successfully to back up the email inbox?
I have found if you go to the enterprise applications in 0365, you can check the signing logs for the application to see if authentications to it were successful.
Yes, if the tenant has access to the MailItemsAccessed record in the UAL, it will show events of that type that are attributed to the service principal ID of PDS.
Fortunately in my company, when the threat actor attempted to register this application, they were blocked. We have conditional access policies, as well as this was not an elevated user account.
When the threat actor phished the account credentials, the user authenticated the MFA request because it appeared they attempted to log in to a Microsoft site. However this was not the case. The threat actor then proceeded to disable the user’s MFA device and registered their own MFA device.
App: PERFECTDATA SOFTWARE
Activity: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.2; WOW64; Trident/7.0; .NET4.0C; .NET4.0E; Tablet PC 2.0)
authStatus: Failure
Failure reason: Device is not in required device state: {state}. Conditional Access policy requires a compliant device, and the device is not compliant. The user must enroll their device with an approved MDM provider like Intune.
Thank you for this post, it has helped us a lot during an incident.
Also, this is what we used to be able to to finally find what I believe is evidence that PERFECTDATA SOFTWARE was used to download email.
https://learn.microsoft.com/en-us/purview/audit-log-investigate-accounts
We used this command with the known dates, the userID of the user and the AppID that we pulled from applications in Azure AD. We found many hundreds of matches and in the end we have to assume everything was accessed. Luckily for us, it only happened to one, non-privleged, user.
Search-UnifiedAuditLog -StartDate -EndDate -UserIds -Operations MailItemsAccessed -ResultSize 5000 | Where {$_.AuditData -like ‘*”AppId”:””*’} | FL | Export-Csv c:\temp\filename.csv