I remember the first time that I encountered malware. It was 2010, I was 11 years old, and something was wrong with my pink Toshiba Satellite U505.
I don’t remember exactly what it was, but I remember crying to my dad that something scary was happening. He called my older cousin who worked at a computer repair shop and she was able to remove the virus that had infected my beloved laptop. Finally, I could return to playing Neopets and posting MS Paint art on DeviantArt in peace.
But I never forgot. I was careful online, quickly learning how to avoid malware the best I could.
Now the year is 2023, I am 24 years old, and one of my favorite pastimes is infecting my computer with malware.
Oh, how we grow!

But… Why?
I don’t remember exactly when I started doing this. It was during my IT diploma and after I had already learned a fair amount about computers and using virtual machines. I initially found my malware by downloading the newest torrents in the Windows software category on The Pirate Bay. I used one of my VMs for class, ran the malware, and watched what unfolded. I also enjoyed trying to remove all the malware after thoroughly infecting a machine, using tools such as the Farbar Recovery Scan Tool to find and remove malware.
Nowadays I don’t have as much time to play with malware as I want. My setup is safer (or at least it was, until the creators of a hardened VirtualBox loader quit updating it) and my analysis methods are more sophisticated, but I still find myself manually scouring the internet for malware.
Here’s how I rank my methods of finding malware from best to worst:
- Download malware from the 365 quarantined emails at work.
(Perhaps an abuse of my admin power, but I would argue that I’m doing threat intelligence by analyzing the malware targeting our organization.) - Search for malware on Shodan.
(Easy to get off track and find lots of other fun things, you find more innocuous servers than malicious ones.) - Download obviously fake crack torrents.
(You need to wait forever for them to download, and most days you’ll find all the torrents give the same malware. Try again next week for something different.) - Google search for ROBLOX hacks and click on every download link on every page.
(This mainly just annoys you with popups and redirects.) - Download malware from some research repository.
(LAME. What’s the fun in that??)
I’m in the mood to play around on Shodan tonight anyway, so I might as well try to find some malware! And yes, I know there are projects to make it easier to find malware via Shodan, I just find this more fun.
Why HFS Servers?
I first found a HFS server with malware in April 2023 when I was searching for vulnerable PaperCut servers in my city. There were some critical vulnerabilities with PaperCut servers and I needed to ensure that the client servers I protected were safe. It was faster for me to see server exposure via Shodan over checking their firewalls. I found something interesting when I used the Shodan query for PaperCut servers in my province, a residential IP with many ports and services open, including a 3CX server which was notable as it had also had a recent critical vulnerability. A honeypot, perhaps? When I went to the IP’s HFS server I quickly found a server full of suspicious files.

Most of the files were benign or very obvious malware, and I happily downloaded them all while spamming my Protonmail address into the login page
Was this server being used to distribute malware, or was it just someone’s repository? I don’t know, but I eventually decided to be a nark and report the server to the ISP. I was curious how the ISP would respond to the report, so I started a web chat session with their helpdesk. A very confused employee eventually forwarded my statement to their security team. A few days later, all files were deleted off the server. Sorry bud! You should have emailed me. >:)
At this point, I was hooked. I created a few queries to cut down the amount of garbage in my results and started searching for HFS servers. I know that searching for other web servers could work, but I just enjoyed the large amount of strange and unhinged garbage I’d find on HFS servers.
The Query
Unfortunately, I am poor, so I only have a basic membership. Since I can’t easily filter out things like tagged honeypots, I exclude a property that most tagged honeypots have. Below is the query I use for my searches, but I will also frequently edit this query to only get results from a country at a time. Do the US for that if you want to find the really weird stuff. I also find that servers tagged ‘cloud’ are more likely to contain malware, usually because they are VPS.
product:”HttpFileServer httpd” -http.component:”ruby” -country:”CN” http.status:200
Yeah, that’s pretty simple. I think excluding servers running Ruby is a good way to remove the majority of tagged honeypots. I also exclude China because in my experience it’s unlikely that you’ll be able to access any of the servers. Even changing my VPN location to China didn’t do anything other than make Shodan mad at me. 🙁
The Setup
For my search, I’m using Firefox on Kali Linux. I also use a VPN as I am visiting strange and malicious websites, and I like to be as safe as possible. I also use a language translation extension on Firefox, as it helps navigate the many results from non-English speaking countries.
Shodan Search Go Brrrrrrrr
I started a timer to see how long it would take me to find something, then I entered my query and started the search. I’ll open all the IPs on a page at a time and navigate to any viewable pages. I immediately went off track looking up Mitel phone system vulnerabilities, but I still found something very quickly after I finished with that. When I cut out the time spent off-track, it took me roughly 3 minutes to find my first suspicious server. Not bad!
User.exe
It was on a Hong Kong server where I found my first hit. The server ran a couple of other services, but the file server was running on port 80.
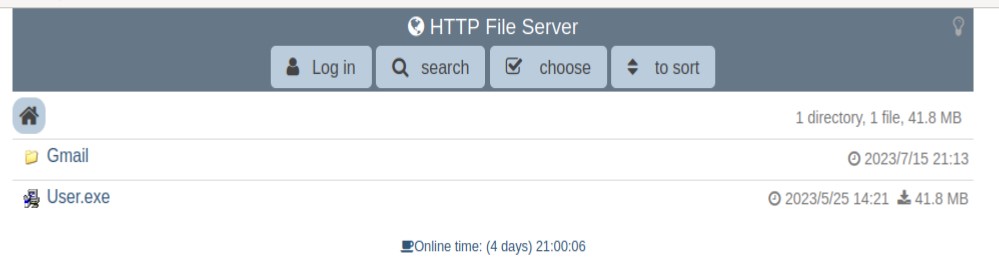
The Gmail folder was empty, but I could download the executable. Uploading it to VirusTotal shows something suspicious, but it could be benign.
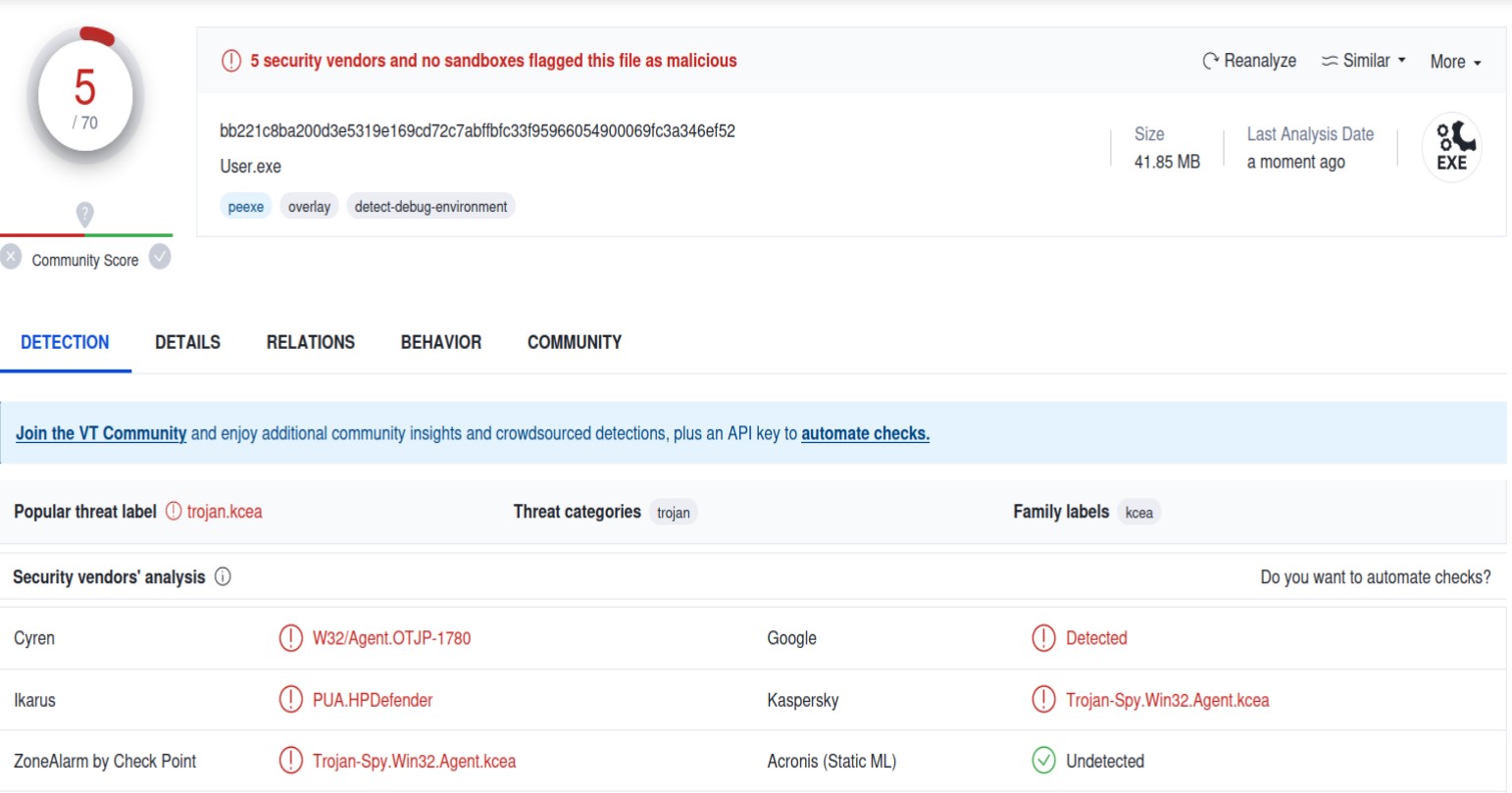
Mirai Botnet
I was concerned when I realized I might have just stumbled upon a Mirai Botnet C2 server. I’m using Linux for this, so I switched to a Windows VM to download the samples.
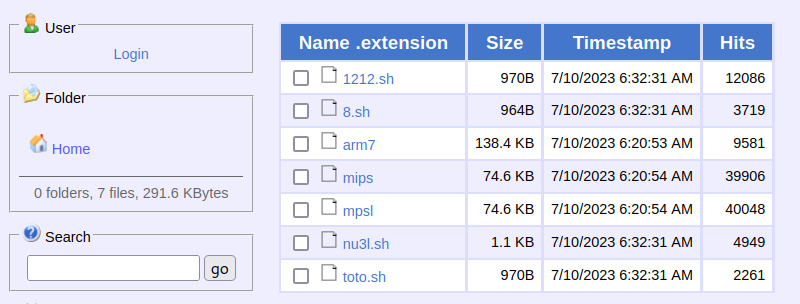
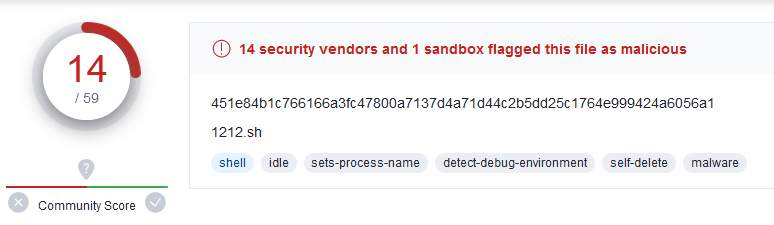
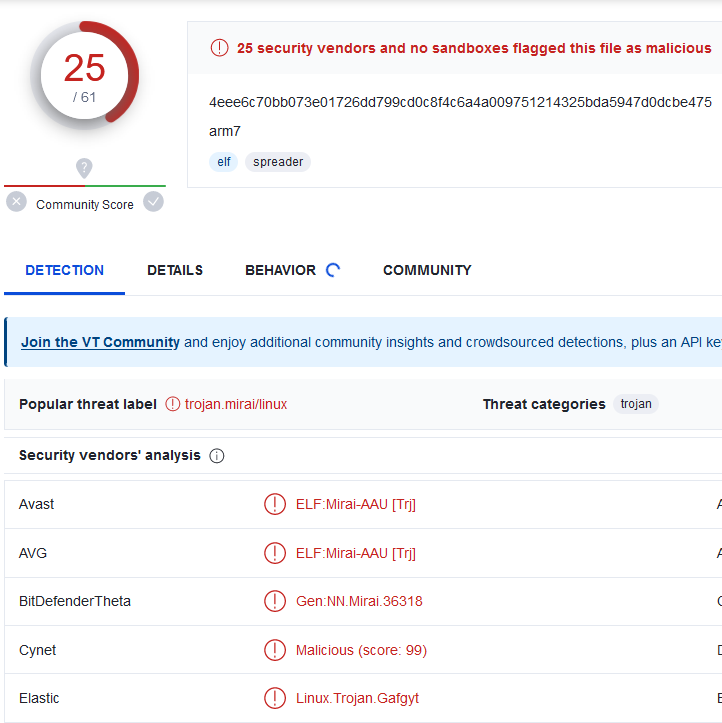
Yeah, that’s not good. I proceeded to go down a week-long rabbit hole of trying to get the host to take down the server, but that’s a story for another time.
Looking Kinda Zusy…
Thankfully it doesn’t look like this sample has been spreading very much. Throwing it into VT gives me this…
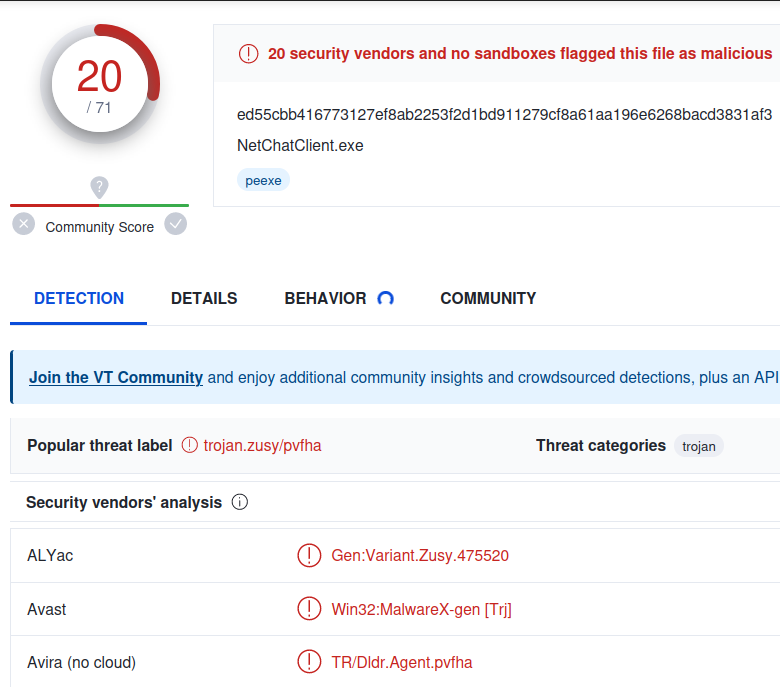
I’m not sure why this malware is sitting on a random file server, but it’s pretty neat!
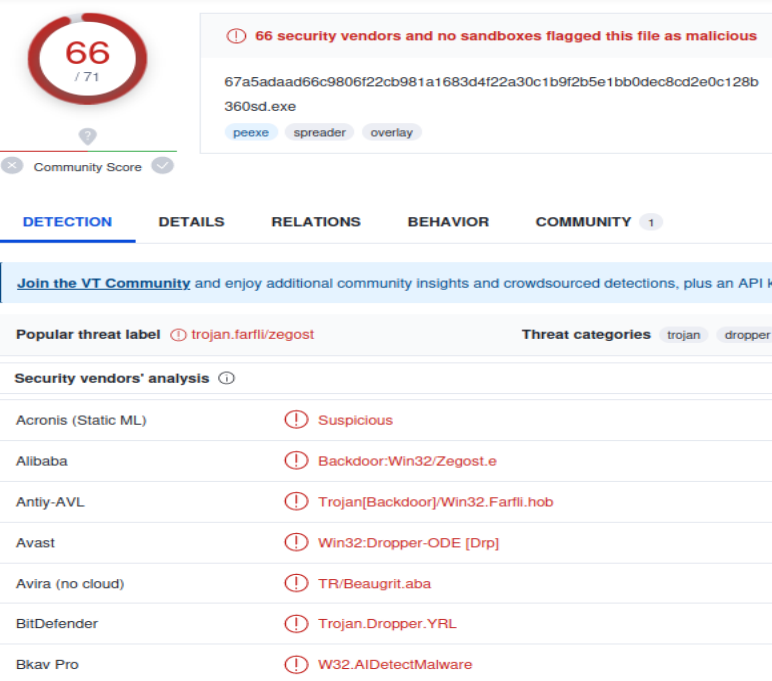
Yet Another Trojan
This one has a few hits, but it’s not spreading too much. Downloading the executables and throwing them into VT shows me some well-known samples that are likely to be caught by nearly every AV product out there.
Non-Malicious
You also find lots of strange stuff when doing this, so I figured I’d post some of it.
Russian JFK

One server contained nothing publicly accessible other than this strange picture of JFK with Russian writing, which I’m assuming is a meme. Alright then…
Free P0rn
A French server contained hundreds of Taiwanese (?) porn videos.
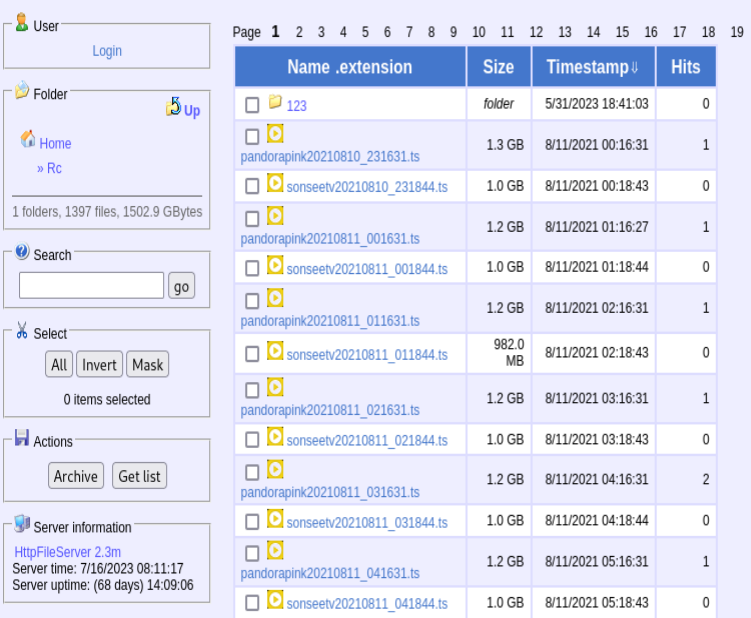
Most videos were over 1GB, but I found one that was a reasonable size to download. In an attempt to keep this blog semi-professional, I’m not going to describe the video, but it was clear what it was within seconds of playing it.

I did have to make a GIF out of the watermark. It’s very funny to me.
So, you can definitely find porn using this Shodan query if that’s the sort of thing you’re into. I won’t judge.
Public Chaos Server
I found a server that invites you to upload random things. It’s mostly used by some friends who play on a Minecraft server on the same host, but anyone can upload!

I’ve blocked out the identifiable usernames and some language I don’t want on my blog.
Some Dude’s Private Keys
I found a file server that contained a private folder and a public zip of that folder. I have censored the names since it’s possible to find the server via the file name.
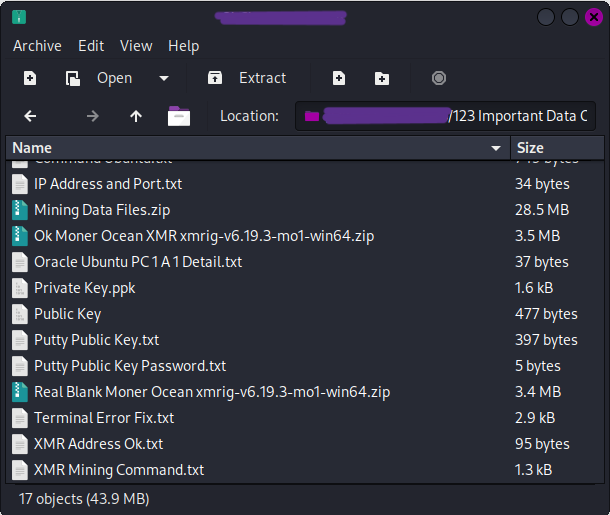
This is definitely not the best thing to have sitting out on a public server. I have to assume that the person behind this doesn’t know that the zip file is publicly accessible. I was feeling altruistic so I attempted to find a way to contact the person, but I was unable to.
Conclusion
After a few hours of searching (over a couple of days), I found lots of interesting things, including an active C2 server. Many servers also had other things running on them, meaning you can go down many rabbit holes. If you’re interested in seeing what’s out there on the internet, don’t care for the more sophisticated ways of finding malware, and just want a fun way to waste a few hours, I suggest trying my query.
I do this occasionally, so I may add or remove things from this post.